| CPC G06F 21/577 (2013.01) [G06N 20/00 (2019.01); G06F 2221/034 (2013.01); G06Q 10/0635 (2013.01); G06Q 10/0637 (2013.01); G06Q 10/06393 (2013.01); G06Q 10/10 (2013.01); G06Q 40/02 (2013.01); G06Q 40/04 (2013.01)] | 20 Claims |
|
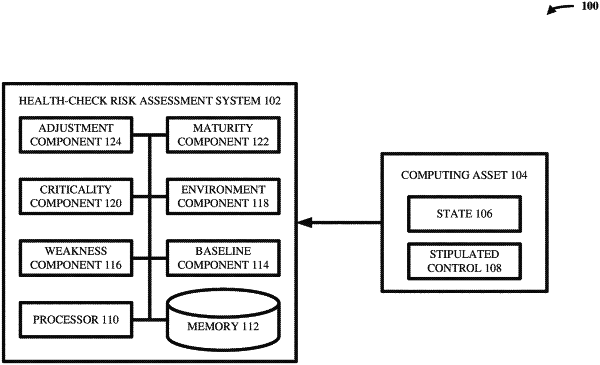
1. A system, comprising:
a processor that executes computer-executable components stored in a memory, the computer-executable components comprising:
a baseline component that generates a baseline health-check risk score corresponding to non-compliance of a computing asset with a stipulated control; and
an adjustment component that:
trains a machine learning model to distinguish respective weakness categories of stipulated controls amongst passive weakness, direct active weakness, and indirect active weakness;
determines, via the machine learning model using natural language processing of technical documentation describing one or more effects resulting from non-compliance of the stipulated control, a weakness category of the stipulated control, wherein the determining comprises:
determining whether the weakness category is the passive weakness,
determining whether the weakness category is the direct active weakness, and
determining whether the weakness category is the indirect active weakness, wherein:
the passive weakness indicates that non-compliance with the stipulated control can enable an attacker to prevent the computing asset from performing an authorized action,
the indirect active weakness indicates that non-compliance with the stipulated control can enable the attacker to perform an unauthorized action with the computing asset, and there is no known exploit of the stipulated control that exists, and
the direct active weakness indicates that non-compliance with the stipulated control can enable the attacker to perform the unauthorized action with the computing asset, and there is a known exploit of the stipulated control that exists;
adjusts the baseline health-check risk score based on a weakness factor of the stipulated control, wherein the weakness factor is based on the weakness category of the stipulated control and a magnitude by which a state of the computing asset deviates from the stipulated control; and
in response to the adjusted baseline health-check risk score satisfying a criterion associated with a predetermined threshold, shut down the computing asset.
|