| CPC G06F 21/564 (2013.01) [G06F 21/552 (2013.01); G06F 21/604 (2013.01)] | 25 Claims |
|
1. A method, comprising:
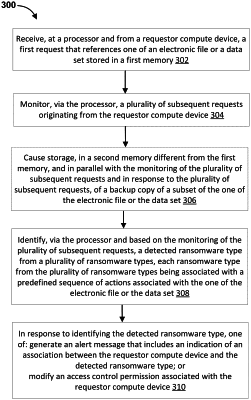
receiving, at a processor and from a requestor compute device, a first request that references one of an electronic file or a data set stored in a first memory, the one of the electronic file or the data set having an associated first set of permissions based on a first role;
monitoring, via the processor, a plurality of subsequent requests originating from the requestor compute device, each subsequent request from the plurality of subsequent requests having an associated subsequent role from a plurality of subsequent roles;
causing storage, in a second memory different from the first memory, and in parallel with the monitoring of the plurality of subsequent requests and in response to the plurality of subsequent requests, of a backup copy of a subset of the one of the electronic file or the data set;
identifying, via the processor and based on the monitoring of the plurality of subsequent requests, a detected ransomware type from a plurality of ransomware types, each ransomware type from the plurality of ransomware types being associated with a predefined sequence of actions associated with the one of the electronic file or the data set;
generating, by the processor, a subsequent set of permissions for the plurality of subsequent roles, the subsequent set of permissions being different from the first set of permissions; and
in response to identifying the detected ransomware type, and based on the subsequent set of permissions,
modifying an access control permission associated with the requestor compute device to define a modified access control permission.
|