| CPC G06F 21/564 (2013.01) [G06F 21/554 (2013.01); G06F 21/568 (2013.01)] | 20 Claims |
|
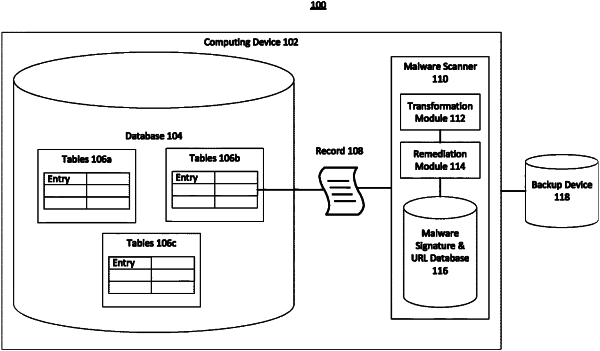
1. A method for detecting malware signatures in a database, the method comprising:
identifying a plurality of entries of the database, wherein each entry represents a record stored on a computing device;
selecting at least one suspicious entry in the plurality of entries;
retrieving a record associated with the suspicious entry;
applying a transformation to original contents of the record, wherein the transformation restructures text in the record;
scanning the transformed contents of the record for a malware signature;
in response to detecting a portion of the transformed contents that matches the malware signature, wherein the portion comprises a malicious function, executing a remediation action that replaces the malicious function in a corresponding portion from the original contents of the record with a harmless function while keeping an input argument of the malicious function unchanged with the harmless function; and
updating the database by replacing the at least one suspicious entry with an entry of the record on which the remediation action was executed.
|