| CPC G06F 21/554 (2013.01) [G06F 21/54 (2013.01); G06F 21/566 (2013.01); G06F 21/577 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
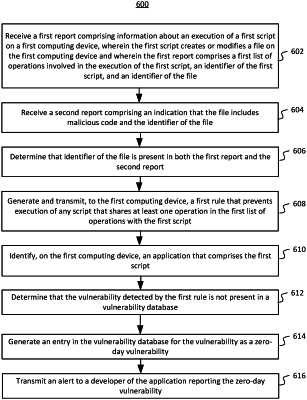
1. A method for preventing zero-day attacks, the method comprising:
receiving a first report comprising information about an execution of a first script on a first computing device, wherein the first script creates or modifies a file on the first computing device and wherein the first report comprises a first list of operations involved in the execution of the first script, an identifier of the first script, and an identifier of the file;
receiving a second report comprising an indication that the file includes malicious code and the identifier of the file;
in response to determining that identifier of the file is present in both the first report and the second report, generating and transmitting, to the first computing device, a first rule that prevents execution of any script that shares at least one operation in the first list of operations with the first script;
identifying, on the first computing device, an application that comprises the first script;
determining whether a vulnerability detected by the first rule is present in a vulnerability database;
in response to determining that the vulnerability is not present in the vulnerability database, generating an entry in the vulnerability database for the vulnerability as a zero-day vulnerability; and
transmitting an alert to a developer of the application reporting the zero-day vulnerability.
|