| CPC G06F 21/554 (2013.01) [G06F 18/214 (2023.01); G06F 21/54 (2013.01); G06F 21/566 (2013.01); G06N 20/00 (2019.01)] | 20 Claims |
|
1. A method comprising:
receiving a data set comprising a plurality of labeled command line inputs;
transforming each of the labeled command line inputs to generate a sequence of individual terms;
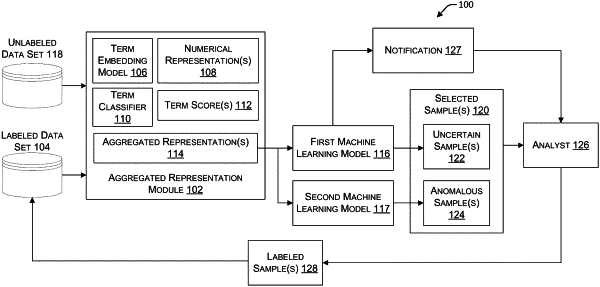
translating each of the sequences of individual terms into a sequence of numerical representations comprising an activity class and a term representation, where individual terms correspond to individual numerical representations, wherein the activity class indicates that a program that is attempting to execute with respect to a term associated with the term representation;
using the activity class to calculate a term score for each of the individual numerical representations based on the individual numerical representations that represents a probability of malicious intent for the corresponding individual term;
generating an aggregated numerical representation comprising at least one of a select number of term scores, a number of terms, a number of rare terms, and the activity class; and
identifying a malicious command line input based on the aggregated numerical representation.
|