| CPC G06F 21/53 (2013.01) [G06F 21/606 (2013.01); G06F 2221/033 (2013.01)] | 18 Claims |
|
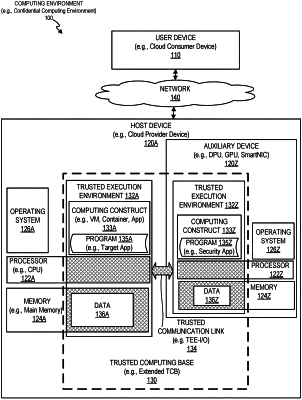
1. A system comprising:
a host device comprising a data processing unit (DPU), the DPU comprising:
a device memory; and
a processor, communicably coupled to the device memory, to perform operations comprising:
determining that the host device comprises a first trusted execution environment established by a central processing unit (CPU) of the host device, wherein the first trusted execution environment comprises memory of the host device and the CPU executes a first computer program in the first trusted execution environment;
establishing a trusted communication link between the first trusted execution environment and a second trusted execution environment, wherein the second trusted execution environment is established by the DPU;
receiving data of the first trusted execution environment using the trusted communication link; and
executing a second computer program in the second trusted execution environment to monitor execution of the first computer program, wherein the second computer program analyzes the data of the first trusted execution environment.
|