| CPC G06F 21/32 (2013.01) [G06F 21/316 (2013.01); G06N 20/00 (2019.01); H04L 63/0853 (2013.01); H04L 63/102 (2013.01); H04L 63/1408 (2013.01)] | 20 Claims |
|
1. A method comprising:
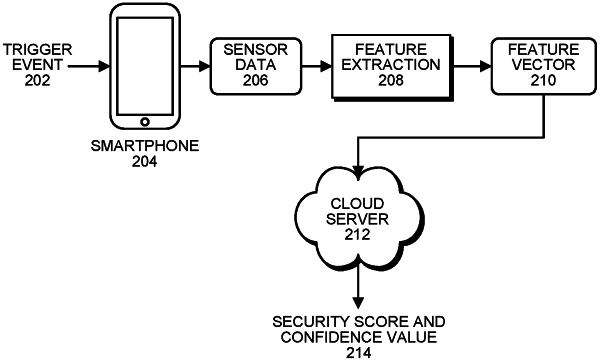
receiving, at an authentication system, a set of feature vectors extracted from a set of sensors of an electronic device;
responsive to analyzing, at the authentication system, the set of feature vectors and/or a set of models of a set of behaviors of a user, determining, by the authentication system, a confidence value to indicate a likelihood that the user is in possession of the electronic device based, at least in part, on the set of feature vectors and/or the set of models;
responsive to the electronic device encountering a login form of a third party, modifying, by the authentication system, the login form through an alteration of a document object model, a structure, a look, a styling, or a combination thereof, of the login form;
responsive to the confidence value exceeding a threshold, authenticating, by the authentication system, the user based, at least in part, on the confidence value and the set of feature vectors and/or the set of models; and
transmitting, by the authentication system, a set of credentials to the third party, wherein:
the set of credentials are stored in memory, and
the set of credentials corresponds to the user.
|