| CPC G06F 21/31 (2013.01) [G06F 21/6218 (2013.01); G06N 20/00 (2019.01)] | 21 Claims |
|
1. A network security system, comprising:
a processor;
a non-transitory, computer-readable storage medium, including computer instructions for:
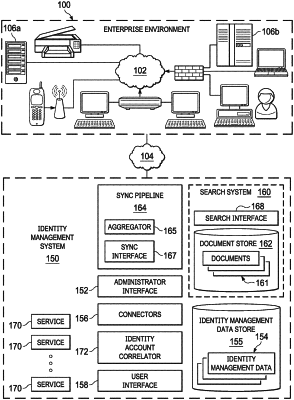
obtaining identity management data associated with a source system in an enterprise computing environment, the identity management data comprising account data on accounts of the source system and identity data on identities of the enterprise computing environment;
determining uncorrelated accounts of the accounts from the source system and correlated accounts from the accounts from the source system, wherein each of the correlated accounts is associated with an identity of the identities from the source system;
determining a similarity measure based on an uncorrelated account of the set of uncorrelated accounts and the set of correlated accounts;
clustering the accounts to determine account clusters, the clustering based on the similarity measure based on the uncorrelated account and the set of correlated accounts, wherein an account cluster of the account clusters comprises the uncorrelated account and one or more correlated accounts;
managing network security of the distributed enterprise computing environment by:
for the uncorrelated account of the uncorrelated accounts, determining the account cluster including the uncorrelated account;
determining a peer correlated account in the account cluster, wherein the peer correlated account is one of the correlated accounts included in the account cluster;
determining a crowdsourcing target based on the peer correlated account, wherein the crowdsourcing target is a first identity associated with the peer correlated account;
sending a crowdsourcing communication associated with the uncorrelated account to the crowdsourcing target;
determining a response to the crowdsourcing communication associated with the uncorrelated account; and
managing network security of the enterprise computing environment by managing access of the uncorrelated account within the enterprise computing environment based on the response.
|