| CPC G06F 21/00 (2013.01) [G06F 21/126 (2013.01); G06F 21/56 (2013.01); G06F 21/563 (2013.01); G06F 21/566 (2013.01); G06F 21/121 (2013.01); G06F 21/6281 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
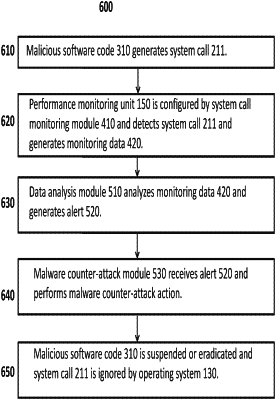
1. A system for identifying and analyzing system calls to identify potentially malicious software code, the system comprising:
a processor comprising a performance monitoring unit and configured to run an operating system, the operating system comprising a kernel;
a system call monitoring module, executed by the processor, for configuring the performance monitoring unit to:
identify a system call and one or more hardware interrupts to the kernel, by trapping one or more FAR branches that are destined for the kernel, thereby allowing the system to encapsulate a system call instruction that generates the system call and one or more hardware interrupts, wherein the system call comprises the one or more FAR branches; and
generate monitoring data from the system call; and
a data analysis module, executed by the processor, to analyze the monitoring data in light of previously stored data, to learn from the previously stored data and the monitoring data, and to generate an alert based on the monitoring data, the alert indicating that the system call was generated by potentially malicious software code.
|