| CPC H04L 9/3242 (2013.01) [G08G 1/22 (2013.01); H04L 9/0637 (2013.01); H04L 9/0643 (2013.01); H04L 9/12 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3297 (2013.01); H04L 2101/622 (2022.05); H04L 2209/80 (2013.01); H04L 2209/84 (2013.01)] | 16 Claims |
|
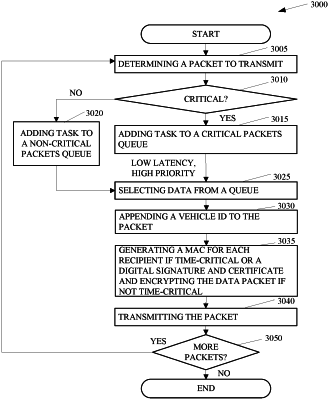
1. An apparatus, comprising:
wireless communication circuitry;
processing circuitry; and
a memory device, storing a leader vehicle symmetric encryption key (SEK) associated with a leader vehicle in a platoon of vehicles, a first SEK associated with a first follower vehicle in the platoon of vehicles, a second SEK associated with a second follower vehicle in the platoon of vehicles, and a third SEK associated with a third follower vehicle in the platoon of vehicles, and instructions executable by the processing circuitry, which when executed cause the processing circuitry to:
generate a first message authentication code (MAC) for a data packet with the first SEK;
generate a second MAC for the data packet with the second SEK;
generate a third MAC for the data packet with the third SEK;
transmit the data packet with the first MAC, the second MAC, and the third MAC to the first follower vehicle via the wireless communication circuitry;
determine whether the data packet is time critical;
compute the first MAC, the second MAC, and the third MAC based on a secure hash algorithm (SHA) responsive to a determination that the data packet is time critical; and
encrypt a payload portion of the data packet responsive to a determination that the data packet is not time critical.
|