| CPC H04L 9/0822 (2013.01) [G06F 12/0813 (2013.01); G06F 12/123 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); G06F 2212/60 (2013.01); G06F 2212/62 (2013.01)] | 18 Claims |
|
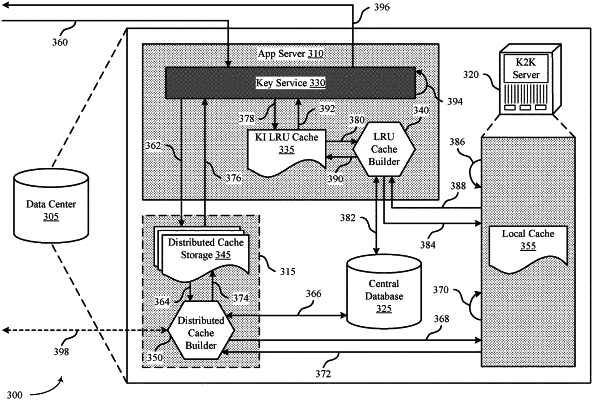
1. A method for data encryption, comprising:
receiving, from an application server, a data encryption key request at a distributed cache;
receiving, from a central database and at the distributed cache, an encryption key parameter corresponding to a user based at least in part on the data encryption key request;
transmitting an additional data encryption key request to a key derivation server, the additional data encryption key request comprising the encryption key parameter and triggering a key derivation procedure;
receiving, at the distributed cache as a result of the key derivation procedure, a first encryption key that is encrypted by a second encryption key, wherein the second encryption key is inaccessible by the distributed cache;
transmitting the first encryption key that is encrypted by the second encryption key to an application server remote from the distributed cache based at least in part on receiving the data encryption key request;
receiving, from the application server, a destruction request message to destroy the encryption key parameter; and
removing, based at least in part on the destruction request message, the first encryption key that is stored at a key cache associated with the distributed cache and encrypted by the second encryption key.
|