| CPC G11C 29/10 (2013.01) [G06F 3/0619 (2013.01); G06F 3/0659 (2013.01); G06F 3/0679 (2013.01); G06F 11/2094 (2013.01); G06F 11/3037 (2013.01); G11C 16/26 (2013.01); G11C 16/349 (2013.01); G11C 16/0483 (2013.01)] | 20 Claims |
|
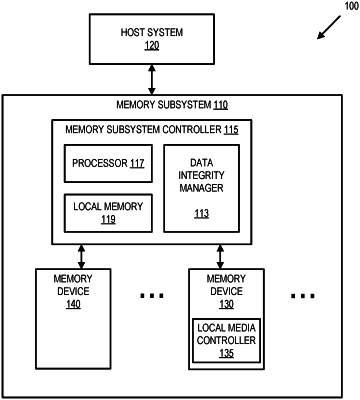
1. A method comprising:
receiving a plurality of read operations, the plurality of read operations divided into a current set of a sequence of read operations and one or more other sets of sequences of read operations;
selecting an aggressor read operation from the current set;
storing an identifier of the aggressor upon reaching the aggressor read operation in the sequence of read operations in the current set;
determining a position in the sequence of read operations in the current set that is preceded by at least a minimum number of read operations following a previous data integrity scan in a previous set of read operations; and
using the stored identifier to perform a current data integrity scan on a victim of the aggressor read operation at the determined position in the sequence.
|