| CPC G06N 20/00 (2019.01) [H04L 63/0428 (2013.01); H04N 21/44008 (2013.01); H04N 21/4408 (2013.01)] | 20 Claims |
|
1. A device, comprising:
a processing system including a processor; and
a memory that stores executable instructions that, when executed by the processing system, facilitate performance of operations, the operations comprising:
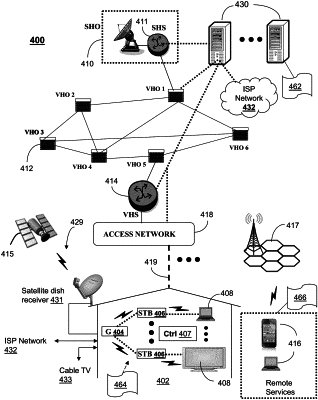
deriving a first set of traffic feature vectors from encrypted network traffic flow data that is collected, wherein the encrypted network traffic flow data is from user interaction with an application, and wherein each traffic feature vector in the first set of traffic feature vectors is derived from a plurality of traffic counters;
applying a generative model to the first set of traffic feature vectors to generate a second set of traffic feature vectors, wherein the second set of traffic feature vectors has statistic properties that are the same as statistic properties of the first set of traffic feature vectors, wherein the second set of traffic feature vectors is larger than the first set of traffic feature vectors, and wherein the second set of traffic feature vectors includes the first set of traffic feature vectors;
training a machine learning algorithm on the second set of traffic feature vectors to classify each traffic feature vector in the second set of traffic feature vectors as associated with a type of the application or not associated with the type of the application; and
classifying whether an encrypted network traffic flow is associated with the type of the application by applying the machine learning algorithm to a traffic feature vector of the encrypted network traffic flow.
|