| CPC G06F 21/6254 (2013.01) [G06F 21/602 (2013.01); G06F 21/78 (2013.01); H04L 9/008 (2013.01); H04L 9/0825 (2013.01); H04L 9/0844 (2013.01); H04L 9/0866 (2013.01); H04L 9/3247 (2013.01)] | 32 Claims |
|
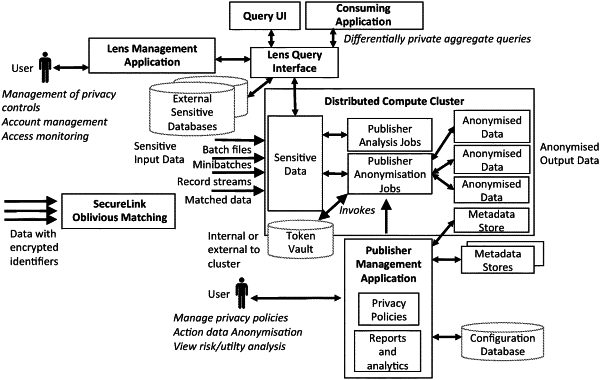
1. A computer implemented method for securely sharing datasets that include information and an original unique ID associated with an individual, where the datasets originate from several different data contributors and are to be shared with a central party or recipient, while concealing or masking the original, unique ID;
in which each contributor randomly encrypts the original, unique ID and sends the encrypted original unique ID to an intermediary party, together with the information associated with each individual, so that each data record or batch or data release will contain a different encrypted form of the original unique ID associated with that individual, in which the encryption is performed with both a public key of the central party and a public key of the intermediary party;
the intermediary party performs a homomorphic crypto operation that deterministically but irreversibly maps the encrypted original, unique ID to an encrypted and obscured form that differs for each contributor, and sends that encrypted and obscured data to a central or recipient party in which the homomorphic crypto operation uses a blind homomorphic operation, and in which the intermediary party uses the same exponentiation key k for all contributors when performing the homomorphic crypto operation;
the central or recipient party (i) decrypts using its private key the encrypted and obscured data received from the intermediate party to recover obscured unique IDs that are one-to-one mapped to but cannot be used to recover the original, unique ID and then (ii) joins together the information for the individual from each contributor.
|