| CPC G06F 21/566 (2013.01) [G06F 16/1734 (2019.01); G06F 16/182 (2019.01); G06F 21/565 (2013.01); G06N 20/00 (2019.01); G06F 2221/034 (2013.01)] | 18 Claims |
|
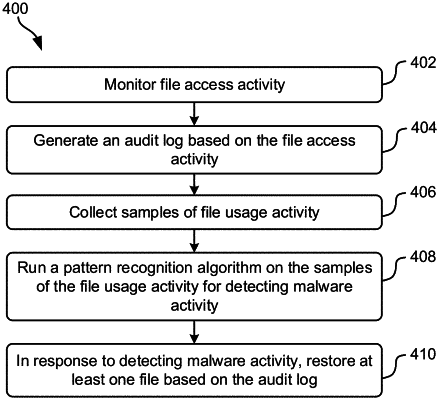
1. A computer-implemented method, comprising:
monitoring file access activity on nodes in a distributed file system comprising a server in communication with the nodes;
generating an audit log based on the file access activity on the nodes;
periodically collecting samples of file usage activity over predefined windows of time from the nodes, wherein the windows of time are cumulatively less than a duration of the monitoring, wherein the nodes locally process events that are collected over a period of time in memory buffers in the respective nodes;
running a pattern recognition algorithm on the samples of the file usage activity for detecting malware activity;
in response to detecting malware activity, restoring at least one file based on the audit log; and
in response to detecting suspected malware activity, modifying a file of one of the nodes, performing a detailed analysis of the modified file, wherein the detailed analysis is performed by a different node than the node on which the modified file is stored.
|