| CPC G06F 21/56 (2013.01) [G06F 9/30061 (2013.01); G06F 9/448 (2018.02); G06F 11/3636 (2013.01); G06F 12/1009 (2013.01); G06F 21/566 (2013.01); H04L 63/145 (2013.01); H04L 63/1441 (2013.01)] | 21 Claims |
|
8. A method for detecting malware comprising:
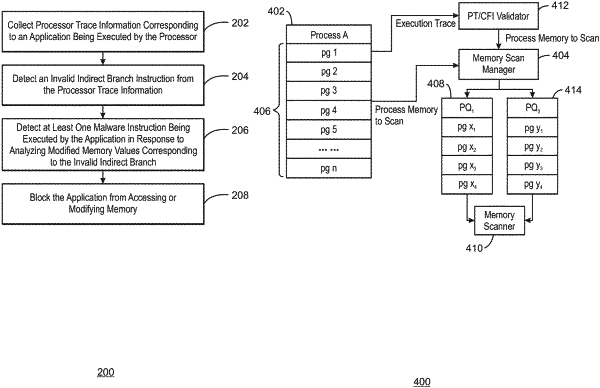
collecting processor trace information corresponding to instructions for an application being executed by a processor, the instructions to include an indirect branch instruction, the processor trace information to indicate a memory address of the indirect branch instruction;
determining whether the memory address of the indirect branch instruction is listed in a set of allowed target addresses for the indirect branch instruction;
detecting a control flow integrity (CFI) violation of a CFI policy associated with the application being executed by the processor when the memory address of the indirect branch instruction is not listed in the set of allowed target addresses for the indirect branch instruction;
initiating scanning of executed memory pages associated with the application being executed by the processor in response to detection of the CFI violation, the memory pages organized into different priority queues to prioritize an order for the memory page scans;
detecting at least one malware instruction being executed by the application in response to scanning the memory pages organized into the different priority queues; and
blocking the application from accessing or modifying memory.
|