| CPC G06F 21/14 (2013.01) [G06F 8/443 (2013.01); G06F 8/51 (2013.01)] | 19 Claims |
|
1. A system comprising:
a processor; and
memory coupled to the processor and storing instructions that, when executed by the processor, cause the system to perform operations comprising:
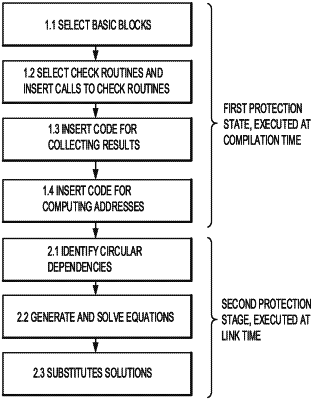
selecting at least two basic blocks from a plurality of basic blocks for a compilation unit;
selecting a check routine that returns a check value as a function of an area of memory of the selected at least two basic blocks; and
inserting code into the selected at least two basic blocks to compute a starting address of a next basic block to be executed based on a result collected from the selected check routine,
wherein each basic block is located at a respective starting address, wherein selecting the at least two basic blocks, selecting the check routine, and inserting the code to dynamically compute the starting address are performed at compilation time for a piece of software.
|