| CPC H04L 63/123 (2013.01) [G06F 8/30 (2013.01); G06F 21/33 (2013.01); G06F 21/602 (2013.01); G06F 21/629 (2013.01); H04L 9/3213 (2013.01); H04L 9/3234 (2013.01); H04L 9/3236 (2013.01); H04L 9/3239 (2013.01); H04L 9/3271 (2013.01); H04L 63/0281 (2013.01); H04L 63/0807 (2013.01); H04L 63/0884 (2013.01); H04L 63/10 (2013.01); H04L 63/101 (2013.01); H04L 63/108 (2013.01); H04W 12/069 (2021.01); H04W 12/08 (2013.01); H04W 12/122 (2021.01); H04L 2463/121 (2013.01)] | 19 Claims |
|
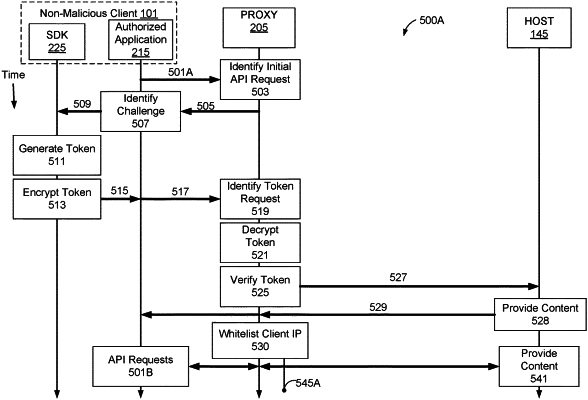
1. A computer implemented method for authenticating a client device to access an application programming interface (API) of a host device by a proxy, the method comprising:
determining that a first API request lacks a form of authentication including lacking a token where the first API request cannot be authenticated due to not including the form of authentication, wherein the first API request is received from the client device;
denying the first API request in response to the first API request lacking the form of authentication;
transmitting a challenge to the client device in response to the denial of the first API request;
determining that a second API request includes a presented token as the form of authentication, the second API request received from the client device;
verifying the presented token of the second API request based on attributes of the presented token;
in response to the presented token being verified, permitting the second API request; storing an IP-token pair comprising an internet protocol (IP) address of the client device stored in association with the presented token; and
transmitting the permitted second API request to the host device for servicing.
|