| CPC H04L 63/20 (2013.01) [H04W 12/03 (2021.01); H04W 12/06 (2013.01)] | 19 Claims |
|
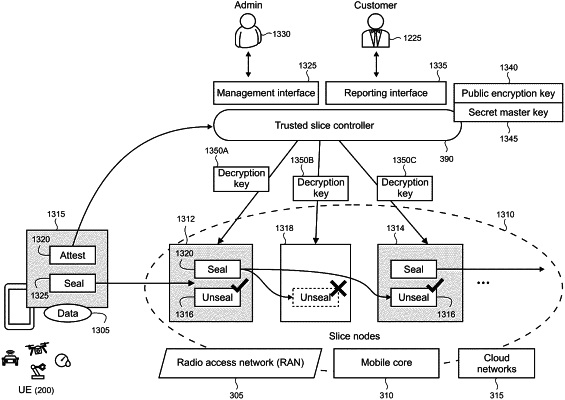
1. A computer-implemented method for implementing a trust model across physical infrastructure of a 5G (fifth generation) network having a plurality of slices, the method comprising:
distributing a plurality of trusted execution environments (TEEs) in the physical infrastructure comprising nodes of a trusted slice among the plurality of slices;
binding data from a data source to the physical infrastructure of the trusted slice to seal the data in the trusted slice in which sealed data is encrypted based on a policy describing a node configuration;
configuring TEEs in the trusted slice to decrypt and forward the sealed data for delivery to a destination of the 5G network, wherein each of the TEEs is configured to successfully decrypt the sealed data responsively to a configuration of the node conforming to the policy; and
providing seal and unseal cryptographic primitives to implement the data binding to the trusted slice.
|