| CPC H04L 63/1425 (2013.01) [H04L 63/0227 (2013.01); H04L 63/0236 (2013.01); H04L 63/0263 (2013.01); H04L 63/12 (2013.01); H04L 63/1416 (2013.01); H04L 63/1441 (2013.01); H04L 43/028 (2013.01)] | 60 Claims |
|
1. A method configured to minimize latency between when a packet corresponding to a network threat crosses a boundary between a protected network and an unprotected network and when the network threat is included in an ordered list of network threats, the method comprising:
receiving, by a packet-filtering device providing an interface across the boundary and from a second device, a plurality of packet-filtering rules to be applied, by the packet-filtering device, to all network traffic traversing the boundary, wherein the plurality of packet-filtering rules were generated based on a plurality of network-threat-intelligence reports supplied by a plurality of independent network-threat-intelligence providers, wherein each network-threat-intelligence report comprises one or more network threat indicators each comprising at least one respective network address that has been previously determined, by one or more of the plurality of independent network-threat-intelligence providers, to be associated with a potential network threat, and wherein a first packet-filtering rule of the plurality of packet-filtering rules specifies one or more first packet-matching criteria corresponding to one or more first network-threat indicators associated with a first potential network threat;
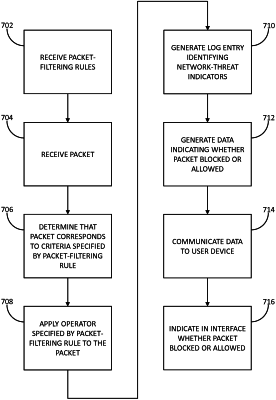
receiving a first packet crossing the boundary between the protected network and the unprotected network;
filtering the first packet based on comparing the first packet to packet-matching criteria specified by the plurality of packet-filtering rules, wherein filtering the first packet comprises determining that the first packet corresponds to the one or more first network-threat indicators associated with the first potential network threat;
responsive to a determination that the filtered first packet matches the first packet-matching criteria of the first packet-filtering rule, and when the filtered first packet corresponding to the first potential network threat is filtered by the packet-filtering device, generating:
a first log entry corresponding to the first potential network threat, and
a first score for the first potential network threat based on information associated with the first potential network threat;
sending, to the second device, the first log entry;
causing the first log entry to be added to the ordered list of network threats, wherein an ordering of the ordered list of network threats is determined based on the first score for the first potential network threat;
receiving, from the second device, an update configured to cause the packet-filtering device to reconfigure the first packet-filtering rule to affect scoring of network threats associated with the first packet-filtering rule;
receiving a second packet crossing the boundary between the protected network and the unprotected network;
filtering the second packet based on the reconfigured first packet-filtering rule, wherein filtering the second packet comprises determining that the second packet corresponds to the one or more first network-threat indicators associated with the first potential network threat;
generating, based on the filtering the second packet and based on the reconfigured first packet-filtering rule:
a second log entry corresponding to the first potential network threat, and
a second score for the first potential network threat different from the first score;
causing a modification to the ordering of the ordered list of network threats based on the first score and the second score; and
causing display of the ordered list of network threats.
|