| CPC H04L 63/1416 (2013.01) [H04L 43/062 (2013.01); H04L 47/2441 (2013.01); H04L 47/2483 (2013.01); H04L 63/0236 (2013.01); H04L 63/1425 (2013.01)] | 15 Claims |
|
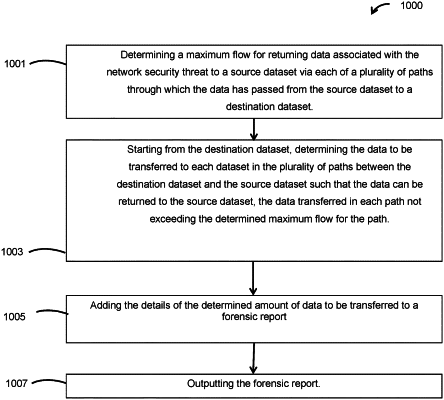
1. A computer-implemented method for reconstructing a dataset after detection of a network security threat in a network, the method comprising:
determining a maximum flow for returning data associated with the network security threat to a source dataset via each of a plurality of paths through which the data has passed from the source dataset to a destination dataset;
starting from the destination dataset, determining an amount of the data associated with the network security threat to be transferred to each dataset in the plurality of paths between the destination dataset and the source dataset such that the data associated with the network security threat can be returned to the source dataset, wherein the data associated with the network security threat to be transferred in each path is less than or equal to the determined maximum flow for the path;
generating a forensic report based on the determined amount of the data associated with the network security threat to be transferred to each dataset a forensic report; and
outputting the forensic report.
|