| CPC H04L 63/102 (2013.01) [H04L 63/083 (2013.01); H04L 63/108 (2013.01); H04L 63/20 (2013.01)] | 21 Claims |
|
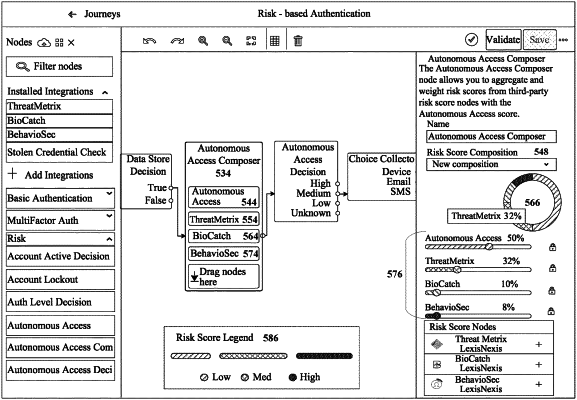
1. A computer-implemented method of aggregating 3rd-party risk measures during an authentication journey, including:
providing a risk measure aggregation node, a J SON transform, and a configuration for requesting 3rd-party risk measures;
responsive to invocation of the risk measure aggregation node during the authentication journey:
setting a timer for receipt of a configured 3rd-party risk measure, wherein expiration of the timer causes the risk measure aggregation node to stop waiting for a timed-out 3 party risk measure provider;
requesting the configured 3rd-party risk measures;
receiving at least some of the requested 3″-party risk measures;
applying the J SON transform to aggregate the received 3rd-party risk measures into an aggregate score; and
the risk measure aggregation node providing to another node in the authentication journey an aggregated score taking into account on the configured 3″-party risk measures received prior to expiration of the timer.
|