| CPC H04L 63/101 (2013.01) [G06F 11/1464 (2013.01); G06F 11/1469 (2013.01); G06F 21/105 (2013.01); H04L 63/0435 (2013.01); H04L 63/102 (2013.01); H04L 63/20 (2013.01); H04L 67/1097 (2013.01); G06F 21/1075 (2023.08)] | 15 Claims |
|
1. An edge device, comprising:
a processor configured with processor-executable instructions to:
receive in a security daemon a security policy for a software application from a secure container platform;
retrieve in a security daemon a license associated with the software application;
determine permissions of the software application based on the retrieved license;
create a user or group account, and update a system service access-control list (ACL), based on the received security policy and the determined permissions;
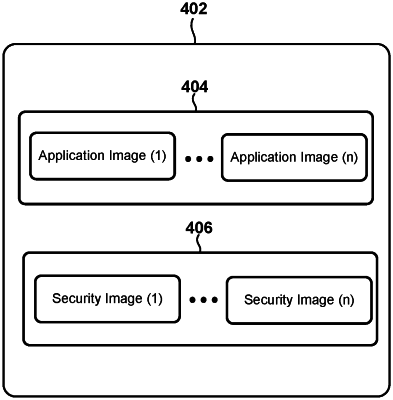
obtain one or more application images of the software application;
obtain one or more security images for the software application;
generate a container package that includes the one or more application images and the one or more security images;
generate and send a policy ready message that includes the generated container package to the secure container platform in response to creating the user or group account and updating the system service ACL, the secure container platform generating a secure container and applying the security policy to the secure container based on information included in the policy ready message;
assign, by the security daemon, hardware resources and system resources to the secure container; and
generate and send, by the security daemon, a policy applied message to the secure container platform in response to assigning the hardware resources and the system resources to the secure container.
|