| CPC H04L 41/0816 (2013.01) [H04L 41/0883 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01)] | 10 Claims |
|
1. A method, comprising:
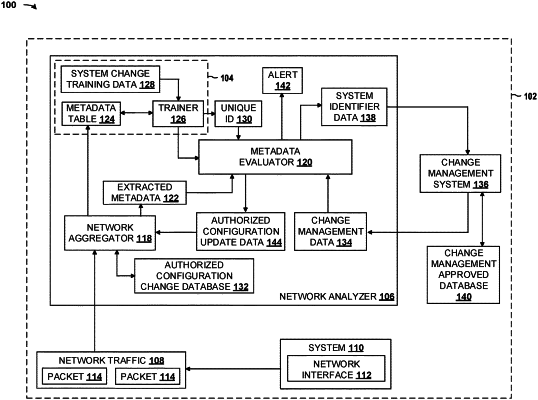
receiving, using a network aggregator, network traffic for a system on a network;
extracting, using the network aggregator, metadata from the network traffic, the metadata being for a system configuration change of the system;
evaluating, using the network aggregator, the metadata relative to a configuration change database to determine whether the system configuration change is an authorized system configuration change based on the metadata;
providing, using the network aggregator, the metadata to a metadata evaluator in response to determining that the system configuration change is not an authorized system configuration change based on the configuration change database;
determining, using a machine learning (ML) model of the metadata evaluator, whether the system configuration change is an authorized system configuration change in response to receiving the metadata, the ML model being trained based on a metadata table and system change data, the metadata table comprising metadata categories for previously received metadata extracted from the network traffic, the metadata categories including authorized and unauthorized metadata categories that are assigned to respective metadata extracted from the network traffic, the system change data identifying authorized and unauthorized system configuration changes for the system; and
causing, using the metadata evaluator, the configuration change database to be updated with the system configuration change in response to the ML model determining that the system configuration change is an authorized system configuration change so that similar future system configuration changes for the system or a different system are authorized by the network aggregator using the configuration change database.
|