| CPC G06Q 20/3678 (2013.01) [H04L 9/083 (2013.01); H04L 9/085 (2013.01); H04L 9/0861 (2013.01); H04L 9/0891 (2013.01); H04L 9/0894 (2013.01); H04L 9/0897 (2013.01); H04L 9/14 (2013.01); H04L 9/3247 (2013.01); H04L 9/50 (2022.05); H04L 2209/56 (2013.01)] | 20 Claims |
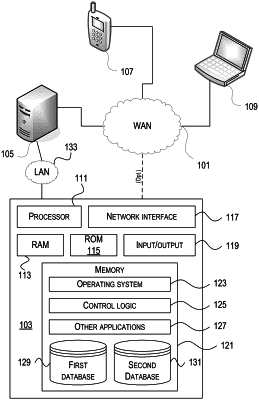
|
1. A method comprising:
receiving, by a computing platform comprising at least one processor, a communication interface, and memory, and from a first user account, a request to transfer cryptocurrency from a first online cryptocurrency wallet for the first user account to a second online cryptocurrency wallet for a second user account;
sending, based on receiving the request to transfer the cryptocurrency, by the computing platform, and to each operator device of a plurality of operator devices corresponding to the first online cryptocurrency wallet, a request for a corresponding share encryption key (SEK) configured to decrypt a corresponding encrypted cryptographic key share configured to reconstruct a cryptographic signing key, wherein the cryptographic signing key is configured to authorize the transfer of the cryptocurrency from the first online cryptocurrency wallet to the second online cryptocurrency wallet;
receiving, by the computing platform and from a first subset of operator devices of the plurality of operator devices, requests to download an encrypted SEK corresponding to each respective operator device of the first subset of operator devices of the plurality of operator devices, wherein the first subset of operator devices of the plurality of operator devices comprises at least a quorum number of operator devices;
sending, by the computing platform and to each operator device of the first subset of operator devices of the plurality of operator devices, a respective encrypted SEK of a plurality of encrypted SEKs;
receiving, by the computing platform and from each operator device of a second subset of operator devices of the plurality of operator devices, a corresponding decrypted SEK decrypted by a respective operator device using a corresponding operator key;
decrypting, using the decrypted SEKs received from the second subset of operator devices of the plurality of operator devices and based on determining that the second subset of operator devices of the plurality of operator devices comprises at least the quorum number of operator devices, corresponding encrypted cryptographic key shares;
reconstructing, by the computing platform and using the decrypted cryptographic key shares, the cryptographic signing key;
validating, by the computing platform, the reconstructed cryptographic signing key; and
based on successful validation of the reconstructed cryptographic signing key, transferring, by the computing platform, the cryptocurrency from the first online cryptocurrency wallet to the second online cryptocurrency wallet.
|