| CPC G06Q 20/108 (2013.01) [G06Q 20/381 (2013.01); G06Q 20/40 (2013.01); G07F 19/00 (2013.01); G06F 3/0482 (2013.01)] | 14 Claims |
|
1. A method comprising:
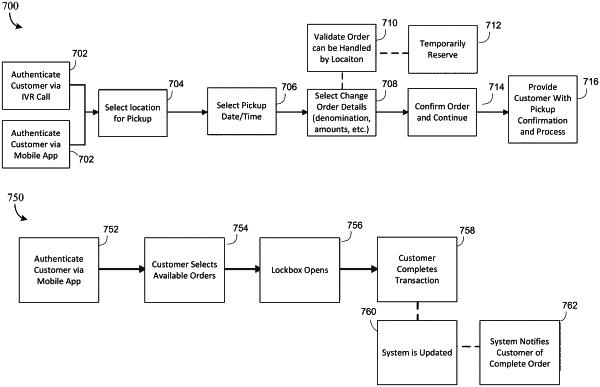
receiving, by a provider computing system of a provider, a first lockbox transaction order associated with an account of the provider from a first user device, the first lockbox transaction order including a first requested transaction and a desired transaction location;
validating, by the provider computing system, whether the first requested transaction can be completed at the desired transaction location;
determining, by the provider computing system based on determining that the first lockbox transaction order cannot be completed at the desired transaction location, a physical lockbox associated with the provider from a plurality of physical lockboxes at an alternative lockbox transaction location;
transmitting, by the provider computing system, an indication to the first user device indicating that the first requested transaction can be completed at the alternative lockbox transaction location;
preparing the physical lockbox for the first requested transaction; and
authenticating, by the provider computing system, a first user at the physical lockbox, wherein the first user is a first account holder of the provider, wherein authenticating the first user at the physical lockbox enables the physical lockbox to unlock and become accessible by the first user;
receiving, by the provider computing system, a second lockbox transaction order from a second user device associated with a second account holder of the provider, the second lockbox transaction order including a second requested transaction;
determining, by the provider computing system, a second authorization level of at least one of the second user device and the second lockbox transaction order, the second authorization level being different from a first authorization level associated with at least one of the first user device and the first account holder;
verifying, by the provider computing system, that an attribute of the second lockbox transaction order conforms to the second authorization level;
preparing the physical lockbox for the second requested transaction;
authenticating, by the provider computing system, the second user at the physical lockbox, wherein authenticating the second user at the physical lockbox enables the physical lockbox to unlock and become accessible by the second user; and
causing, by the provider computing system, a camera to record activity associated with the physical lockbox upon at least one of authenticating the first user at the physical lockbox or authenticating the second user at the physical lockbox.
|