| CPC G06F 8/71 (2013.01) [G06F 8/65 (2013.01); G06F 9/54 (2013.01); G06F 11/3684 (2013.01); G06F 11/3688 (2013.01); G06F 11/3692 (2013.01); G06F 21/577 (2013.01); G06F 21/6218 (2013.01); G06F 2221/033 (2013.01)] | 17 Claims |
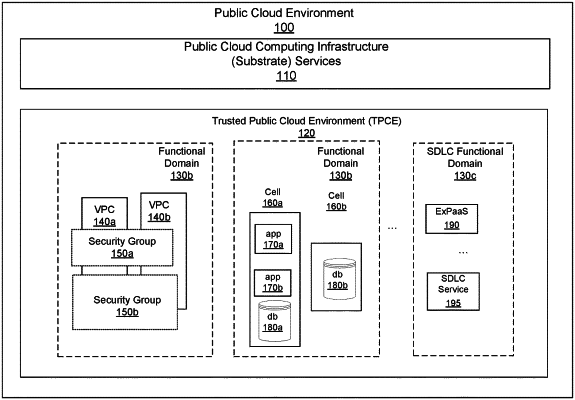
|
1. A computer-implemented method for managing security of applications, the method comprising:
storing a plurality of software bundles, wherein a software bundle includes a plurality of software modules, wherein at least a subset of the software modules of the software bundle have security approval;
receiving, from a user, a criteria for selecting configuration of a potential application;
providing a first software bundle matching the received criteria;
receiving a configuration of the application based on one or more software modules of the first software bundle;
monitoring software development life cycle (SDLC) processes of the application, the monitoring comprising determining whether one or more software modules included in the first software bundle have been customized;
responsive to determining that none of the software modules included in the first software bundle have been customized, automatically granting security approval to the application;
responsive to determining that the one or more software modules included in the first software bundle have been customized, generating a request for security approval based on the one or more software modules included in the first software bundle that have been customized; and
sending the generated request for security approval.
|