| CPC G06F 21/74 (2013.01) [G06F 21/31 (2013.01); G06F 21/602 (2013.01); G06F 21/79 (2013.01); G06F 21/84 (2013.01); G06F 2221/032 (2013.01); G06F 2221/2113 (2013.01)] | 20 Claims |
|
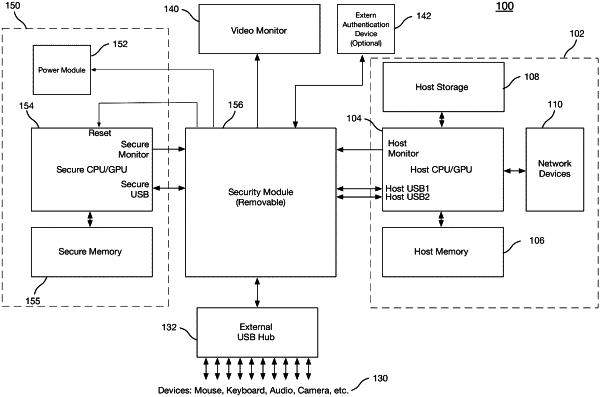
1. A secure computer comprising:
a general-purpose domain configured to provide general-purpose computing, the general-purpose domain comprising: a host processor, a non-volatile storage system, and at least one networking device;
a secure domain configured to provide secure computing, the secure domain comprising:
a secure processor; and
a security module communicatively coupled to and between the general-purpose domain and the secure domain using a peripheral bus protocol, the security module comprising:
a storage encryption module configured to facilitate secure storage data transmission between the general-purpose domain and the secure domain via the peripheral bus protocol, thereby providing the secure domain with secure access to the non-volatile storage system of the general-purpose domain, wherein the storage encryption module is configured to decrypt all incoming storage data packets and encrypt all outgoing storage data packets that are passed between the general-purpose domain and the secure domain and that are communicated with the non-volatile storage system;
a network encryption module configured to facilitate secure network data transmission between the general-purpose domain and the secure domain via the peripheral bus protocol, thereby providing the secure domain with secure access to the at least one networking device of the general-purpose domain, wherein the network encryption module is configured to decrypt all incoming network data packets and encrypt all outgoing network data packets that are passed between the general-purpose domain and the secure domain and that are communicated with the at least one networking device;
and
a context controller configured to enable and disable the storage encryption module and to enable and disable the network encryption module; and
an authentication module configured to authenticate a user of the secure computer before enabling the secure domain.
|