| CPC G06F 21/6245 (2013.01) [G06F 21/554 (2013.01); G06F 21/602 (2013.01); G06N 20/00 (2019.01)] | 19 Claims |
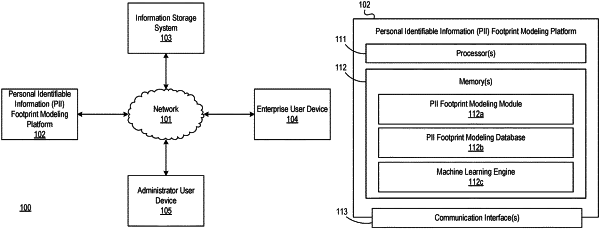
|
1. A user device comprising:
at least one processor;
a communication interface communicatively coupled to the at least one processor; and
memory storing computer-readable instructions that, when executed by the at least one processor, cause the user device to:
receive a request to access information that includes personal identifiable information (PII);
retrieve source data comprising the PII;
mask, within the source data and based on at least one enterprise data management policy, the PII, resulting in masked information;
display the masked information in response to the request to access the information;
receive a request to unmask the masked information;
unmask the PII, resulting in unmasked PII;
display the unmasked PII in response to the request to unmask the masked information; and
send unmasking event information to a PII footprint modeling platform, wherein sending the unmasking event information to the PII footprint modeling platform causes the PII footprint modeling platform to:
log the request to unmask the masked information in an unmasking event log,
apply at least one machine learning model to the unmasking event log to identify one or more malicious events, wherein identifying the one or more malicious events comprises:
identifying that a number of requests for the PII by the user device exceeds a median number of requests for the PII by a predetermined standard deviation of the number of requests, wherein the requests are initiated by other user devices corresponding to users associated with a particular job title and wherein a user of the user device may also be associated with the particular job title, and
trigger one or more remediation actions based on identification of the one or more malicious events, wherein triggering the one or more remediation actions comprises:
based on identifying that the number of requests for the PII by the user device exceeds the median number of requests for the PII by a first standard deviation of the number of requests, temporarily suspending network access to the user device, and
based on identifying that the number of requests for the PII by the user device exceeds the median number of requests for the PII by a second standard deviation of the number of requests, greater than the first standard deviation, modifying a network policy to permanently prevent the user device from accessing the PII.
|