| CPC G06F 21/60 (2013.01) [G06F 2221/2119 (2013.01)] | 20 Claims |
|
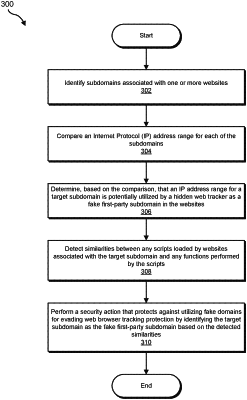
1. A computer-implemented method for protecting user data privacy against the use of fake first-party domains by hidden web trackers, at least a portion of the method being performed by one or more computing devices comprising at least one processor, the method comprising:
identifying, by the one or more computing devices, a plurality of subdomains associated with one or more websites;
comparing, by the one or more computing devices, an Internet Protocol (IP) address range for each of the subdomains;
determining, by the one or more computing devices and based on the comparison, that an IP address range for a target subdomain is potentially utilized by a hidden web tracker as a fake first-party subdomain in the websites;
detecting, by the one or more computing devices, similarities between any scripts loaded by websites associated with the target subdomain and any functions performed by the scripts, wherein detecting the similarities comprises:
applying a fuzzy hashing function to a target subdomain script to generate a first hash result;
applying the fuzzy hashing function to another subdomain script within the IP address range for the target subdomain to generate a second hash result; and
comparing the first and second hash results to generate a similarity score; and
performing, by the one or more computing devices, a security action that protects against utilizing fake domains for evading web browser tracking protection by identifying the target subdomain as the fake first-party subdomain based on the detected similarities.
|