| CPC G06F 21/54 (2013.01) [G06F 21/31 (2013.01); G06F 21/554 (2013.01); G06F 21/562 (2013.01); G06F 21/602 (2013.01)] | 20 Claims |
|
1. A system for computer security, the system comprising:
a target computer;
computer security system software stored in non-transitory storage of the target computer; the computer security system software running on the target computer;
a blacklist accessible by the computer security system software, the blacklist containing entries indicative of which programs are not allowed to run on the target computer;
a program for executing on the target computer;
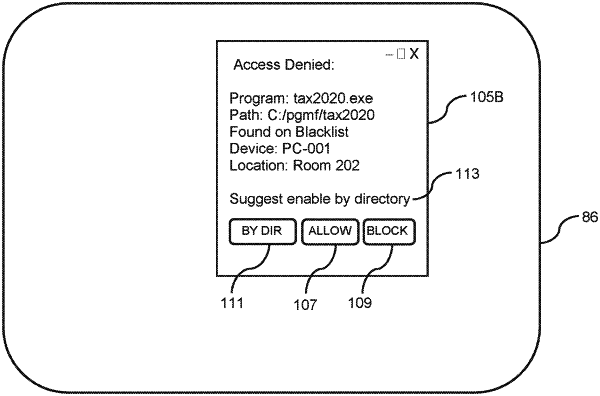
when the program attempts to execute on the target computer, the computer security system software determines whether the program is allowed to run using the blacklist and a whitelist, when the program is not found in the blacklist or the program in found in the whitelist, the computer security system software running on the computer allows the program to run;
otherwise, when the program is found in the blacklist and the program in not found in the whitelist, the program is prevented from running and data regarding the program is captured and stored;
after the program is prevented from running, a set of rules accessible by administrative software determines if the program is within a program classification and when the program is within the program classification, the administrative software presents a user interface for an administrator that includes allowing by the program classification, the administrative software then accepts inputs and upon acceptance of the program classification, the administrative software updates a whitelist to add an override entry that allows execution of the programs in the program classification; and
when the program is not within the program classification, the administrative software presents a second user interface for the administrator that request approval solely for the program and the administrative software then accepts the inputs and upon the acceptance of the program, the administrative software updates the whitelist to add an entry for the program; otherwise, the blacklist is not updated and future attempts to run the program will be blocked.
|