| CPC G06F 21/52 (2013.01) [B01D 15/1885 (2013.01); G01N 30/20 (2013.01); G01N 30/22 (2013.01); G01N 30/466 (2013.01); G01N 30/6043 (2013.01); G06F 11/3688 (2013.01); G01N 2030/202 (2013.01); G01N 2030/207 (2013.01); G06F 2221/033 (2013.01)] | 14 Claims |
|
1. A system for stack pivot exploit detection and mitigation, comprising:
a processor; and
memory storing instructions that, when executed by the processor, causes the system to perform a set of operations for stack pivot detection and mitigation, the set of operations comprising:
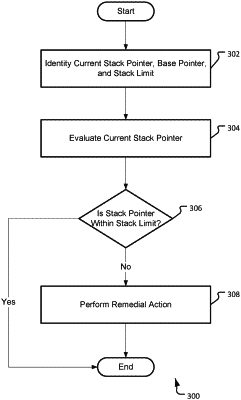
defining, for a process executing in an execution mode, thread information for the process, the thread information comprising a current memory pointer, a memory base, and a memory limit, the memory base and the memory limit defining a memory range for the process;
based on the current memory pointer for the process executing in the execution mode, generating a corresponding memory base pointer for the memory base, and a corresponding memory limit pointer for the memory limit;
comparing the current memory pointer for the thread information to the memory base pointer and the memory limit pointer to determine whether the current memory pointer is within the memory range;
when the current memory pointer is determined to be within the memory range, permitting the process to execute;
when the current memory pointer is determined to not be within the memory range, determining an occurrence of a stack pivot exploit and, in response, performing a remedial action; and
executing a series of checkpoints over time, each checkpoint determining the occurrence of the stack pivot, wherein the execution mode comprises a kernel execution mode, a 32-bit execution mode, and a 64-bit execution mode, each, the execution mode having a corresponding series of checkpoints for determining the occurrence of a stack pivot within each execution mode.
|