| CPC G06F 21/105 (2013.01) [G06F 21/31 (2013.01); H04L 9/30 (2013.01)] | 20 Claims |
|
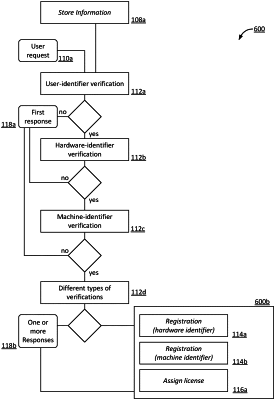
11. A method for providing authentication and authorization for software license management of a particular software-controlled application, the method comprising:
receiving, from a user associated with a client computing device, a user request for user-specific authentication and device-specific authorization to access and/or use the particular software-controlled application, wherein the user request includes:
(a) a user identifier that identifies the user,
(b) a hardware identifier that identifies the client computing device, and
(c) a machine identifier that identifies a cryptographic key, wherein the cryptographic key is a public key used for Public Key Infrastructure (PKI);
performing a user-identifier verification that verifies whether the user identifier in the user request corresponds to one of a set of authorized users that are authorized to access and/or use the particular software-controlled application;
performing a hardware identifier verification that verifies whether the hardware identifier in the user request corresponds to one of a set of registered client computing platforms that have been registered to access and/or use the particular software-controlled application;
performing a machine identifier verification that verifies whether the cryptographic key identified in the machine identifier in the user request is included in a set of registered cryptographic keys, wherein individual registered cryptographic keys of the set of registered cryptographic keys are public keys used for Public Key Infrastructure (PKI), wherein the machine identifier verification uses the public key for Public Key Infrastructure (PKI);
performing a machine revocation verification that verifies whether the machine identifier in the user request corresponds to one of the set of revoked cryptographic keys that have been registered to access and/or use the particular software-controlled application;
performing one of more additional verifications in addition to the user identifier verification, the hardware identifier verification, and the machine identifier verification;
responsive to:
(i) the user identifier verification verifying the user identifier in the user request corresponds to one of the set of authorized users,
(ii) the hardware identifier verification verifying the hardware identifier in the user request corresponds to one of the set of registered client computing platforms,
(iii) the machine identifier verification verifying the cryptographic key identified in the machine identifier in the user request is included in the set of registered cryptographic keys, and
(iv) the one of more additional verifications verifying the user request can be fulfilled, transferring a particular response to the user request, wherein the particular response includes a particular standard HyperText Transfer Protocol (HTTP) status code that indicates the user request has been successful;
responsive to the user identifier verification failing to verify that the user identifier in the user request corresponds to one of the set of authorized users, transferring a first response to the user request, wherein the first response includes a first standard HyperText Transfer Protocol (HTTP) status code that indicates the user request cannot be fulfilled due to error;
responsive to the user identifier verification passing and the hardware identifier verification failing to verify that the hardware identifier in the user request corresponds to one of the set of registered client computing platforms, transfer a second response to the user request, wherein the second response indicates the user request cannot be fulfilled due to error; and
responsive to the user identifier verification passing, the hardware identifier verification passing, and the machine identifier verification failing to verify that the cryptographic key identified in the machine identifier in the user request is included in the set of registered cryptographic keys, transfer a third response to the user request, wherein the third response indicates the user request cannot be fulfilled due to error.
|