| CPC H04W 68/02 (2013.01) [H04W 56/001 (2013.01)] | 6 Claims |
|
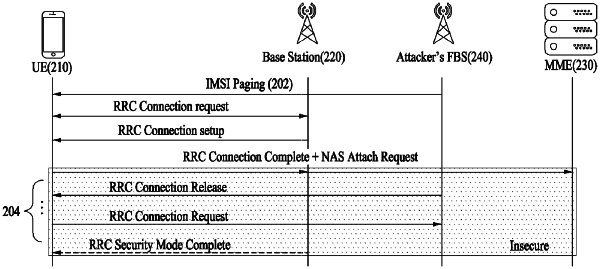
1. A fake base station (FBS) redirection attack method using unicast message injection in a long term evolution (LTE) wireless section, the FBS redirection attack method comprising:
synchronizing a fake base station (FBS) with a signal of a commercial base station connected with a target device being an attack target;
transmitting an international mobile subscriber identity (IMSI) paging message from the FBS to the target device using an IMSI of the target device; and
injecting a unicast message from the FBS including a frequency of the FBS into the target device, before a base station re-access process is completed in the target device which decodes the IMSI paging message,
wherein the synchronizing includes synchronizing with the signal of the commercial base station, in a state where security activation between the target device and the commercial base station is completed,
wherein the injecting of the unicast message includes injecting the unicast message of a radio resource control (RRC) connection release message, before the target device completes a process of re-accessing a base station, and wherein the target device processes the RRC connection release message of plain text, deletes the security context, and requests access from the FBS,
wherein the RRC connection release message includes an IdleModeMobilityControlInfo (IMMCI) field for delivering connection priorities of cells when the target device reselects a cell and a redirectedCarrierInfo field for connecting a user with a specific cell and includes a frequency and an evolved absolute radio frequency channel number (EARFCN) of the FBS in the field.
|