| CPC H04L 9/0894 (2013.01) [G06F 9/45558 (2013.01); H04L 9/0861 (2013.01); H04L 9/3247 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
1. A system, comprising:
one or more processors; and
memory including instructions that, as a result of being executed by the one or more processors, cause the system to:
obtain a request to launch an instance to have privileges associated with a role specified in the request;
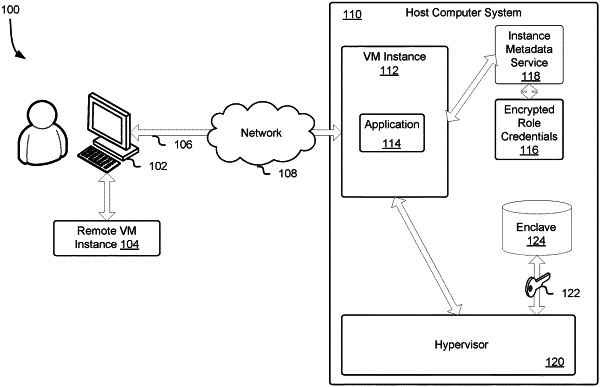
cause a hypervisor to launch the instance on a hardware server;
cause a trusted execution environment to be instantiated for the instance on the hardware server based at least in part on the instance being associated with the role;
as a result of verifying the trusted execution environment based, at least in part, on information obtained from the hypervisor, generate a key specific to the instance and the role;
store the key in the trusted execution environment to protect the key for the instance; and
cause the trusted execution environment to use the key to decrypt encrypted role credentials provided to the instance to sign requests pursuant to the role.
|