| CPC H04L 9/083 (2013.01) [H04L 9/0825 (2013.01); H04L 9/0841 (2013.01); H04L 9/0861 (2013.01); H04L 9/0894 (2013.01); H04L 9/3247 (2013.01)] | 20 Claims |
|
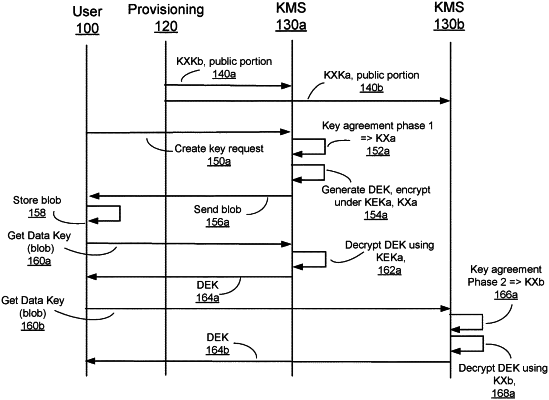
1. A computer implemented method for obtaining an encrypted data encryption key from an instance of a key management system (KMS), the method comprising:
receiving, at a first instance of a KMS, a request for a data encryption key (DEK) from a user, the first instance of the KMS configured with a first symmetric key, a first public-private key pair that is associated with the first instance of the KMS, and a second public key that is obtained from a different second instance of a KMS system to be used in a key agreement scheme between the first and second instances of the KMS;
generating, at the first instance of the KMS, the DEK;
generating, at the first instance of the KMS, a blob, wherein the blob comprises:
a first instance of the generated DEK that is subsequently encrypted by the first symmetric key, and
a second instance of the generated DEK that is subsequently encrypted by a negotiated key that is generated based on the key agreement scheme; and
sending the blob to the user, wherein the first instance of the KMS is configured to decrypt the first instance of the generated DEK and the second instance of the KMS is configured to decrypt the second instance of the DEK.
|