| CPC H04L 9/0825 (2013.01) [H04L 9/0866 (2013.01); H04L 9/14 (2013.01); H04L 67/1095 (2013.01); H04L 67/561 (2022.05)] | 20 Claims |
|
1. A computer-implemented method when executed by data processing hardware of a cloud computing environment causes the data processing hardware to perform operations comprising:
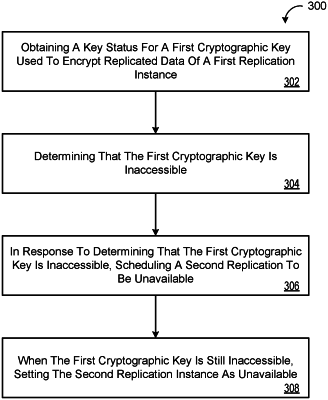
obtaining a key status for a first cryptographic key, the first cryptographic key used to encrypt replicated data of a first replication instance of a cloud data warehouse;
determining, based on the key status, that the first cryptographic key is inaccessible to the data processing hardware, the inaccessible first cryptographic key causing the first replication instance to be unavailable for updates by the data processing hardware;
in response to determining that the first cryptographic key is inaccessible, scheduling a second replication instance of the cloud data warehouse to be unavailable after a threshold amount of time has passed, the second replication instance including replicated data encrypted by a second cryptographic key, the second cryptographic key accessible to the data processing hardware;
determining, after the threshold amount of time has passed, that the first cryptographic key is still inaccessible; and
based on determining that the first cryptographic key is still inaccessible, setting the second replication instance as unavailable to prohibit updates to the second replication instance by the data processing hardware.
|