| CPC H04L 9/0643 (2013.01) [G06F 9/45508 (2013.01); G06F 9/466 (2013.01); G06F 16/9024 (2019.01); H04L 9/50 (2022.05)] | 24 Claims |
|
1. A tangible, non-transitory, machine-readable medium storing instructions that when executed by one or more processors effectuate operations comprising:
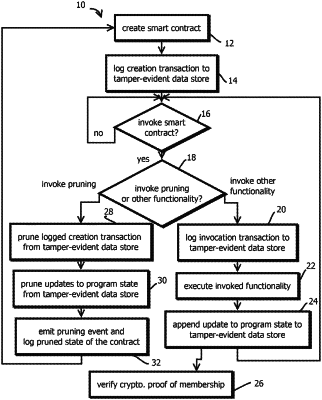
receiving, with a computer system, a request to prune data stored in a tamper-evident data store, wherein:
the data includes first program state of a first program at a first time,
the first program is one of a plurality of programs having program state stored in the tamper-evident data store,
the request uniquely identifies the first program with an identifier that distinguishes the first program from a second program among the plurality of programs,
the tamper-evident data store comprises a directed acyclic graph of cryptographic hash pointers,
a first subset of the cryptographic hash pointers have cryptographic hash values based on the first program state of the first program at the first time,
a second subset of the cryptographic hash pointers have cryptographic hash values based on second program state of the first program at a second time,
a third subset of the cryptographic hash pointers have cryptographic hash values based on the first program state of the first program at the first time, the second program state of the first program at the second time, and a program state of the second program from before the first time, and
the tamper-evident data store comprises or is associated with a record that links the first subset of the cryptographic hash pointers to the second subset of the cryptographic hash pointers;
in response to the request, based on the identifier and the record that links the first subset of the cryptographic hash pointers to the second subset of the cryptographic hash pointers, with the computer system, selecting:
a first subset of nodes of the directed acyclic graph having first content based on the first program state of the first program at the first time, the hash values of first subset of the cryptographic hash pointers being based on the first content, and
a second subset of nodes of the directed acyclic graph having second content based on the second program state of the first program at the second time, the hash values of second subset of the cryptographic hash pointers being based on the second content;
pruning, with the computer system, the first program state and the second program state from the tamper-evident data store by changing the first content and the second content in memory, wherein:
after the pruning, cryptographic hash values of the directed acyclic graph of cryptographic hash pointers are internally consistent, and
after the pruning, the program state of the second program from before the first time remains in the tamper-evident data store.
|