| CPC H04L 63/145 (2013.01) [G06F 21/53 (2013.01)] | 15 Claims |
|
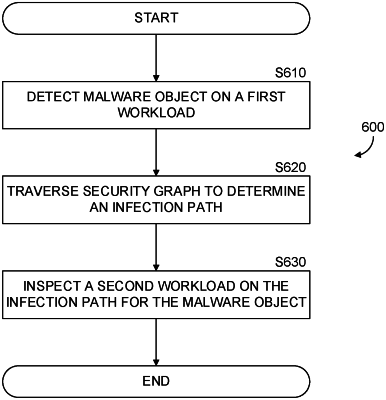
1. A method for detecting a malware infection path in a compute environment, comprising:
detecting a malware object on a first workload in a computing environment, the computing environment including a plurality of workloads, wherein the first workload is represented by a resource node on a security graph, the security graph further including an endpoint node representing access to a public access network;
traversing the security graph from the resource node to the endpoint node to generate a potential infection path between the resource node and the endpoint node;
inspecting a second workload of the plurality of workloads represented by a second resource node for the malware object, wherein the second resource node is on the potential infection path;
determining that the potential infection path is a confirmed infection path, in response to detecting the malware object on the second workload;
determining that the potential infection path is not an infection path, in response to detecting that the second workload does not include the malware object;
generating an impact analysis output of the malware object on the potential infection path, including an identifier of the second workload represented in the security graph by a node connected via a vertex to the node representing the first workload, wherein the vertex indicates that the first workload is configured to access the second workload.
|