| CPC H04L 63/1425 (2013.01) [H04L 41/149 (2022.05); H04L 43/028 (2013.01); H04L 61/2514 (2013.01); H04L 63/1433 (2013.01)] | 18 Claims |
|
1. A computer-implemented method, comprising:
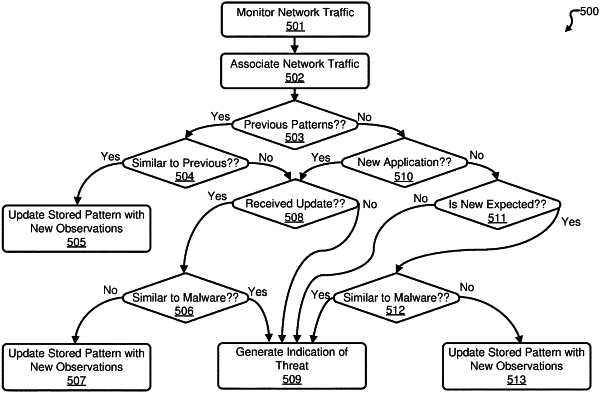
monitoring network traffic on a computer network that includes a plurality of endpoints, wherein the network traffic for each endpoint includes sent data that is transmitted from the endpoint and received data that is received by the endpoint over the computer network;
identifying a software application executing on at least one endpoint from one or more of the sent data or the received data, wherein:
the execution of the software application is associated with at least two time windows, and
the at least two time windows comprise a startup time window and a post-startup time window;
determining a security status score for the at least one endpoint based on a comparison of the sent data and the received data with a known pattern of network activity associated with the software application, wherein the known pattern of network activity is based upon the startup time window of the software application;
wherein determining the security status score includes,
determining a level of match between network traffic features associated with destination IP addresses for the at least one endpoint with the known pattern of network activity, and
adjusting the security status score based on the level of match such that endpoints with destination IP addresses that have a first level of match to the known pattern of network activity are assigned higher security status scores than endpoints that have a second level of match, wherein the first level of match is greater than the second level of match;
determining a threat status for the at least one endpoint based on the security status score; and
generating an indication of the threat status for the at least one endpoint.
|