| CPC H04L 63/1416 (2013.01) [G06F 9/541 (2013.01); G06F 16/2379 (2019.01); G06F 21/577 (2013.01); G06F 21/604 (2013.01); G06F 21/6245 (2013.01); H04L 63/0209 (2013.01); H04L 63/1425 (2013.01); H04L 63/1466 (2013.01); H04L 63/20 (2013.01); G06F 2221/034 (2013.01)] | 12 Claims |
|
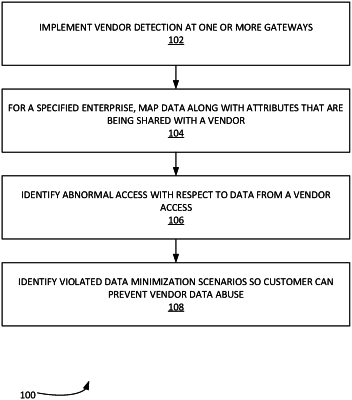
1. A computerized method for automatically identifying and solving for vendor data abuse in an enterprise network, comprising:
implementing a vendor detection at one or more gateways of the enterprise network;
mapping a set of data along with any associated data attributes of the set of data that are being shared with a vendor via the one or more gateways;
detecting and identifying an access anomaly with respect to the set of data associated with a vendor access; and
implementing a specified data minimization process to the access anomaly,
wherein the data minimization process is applied for every vendor sharing agreement engaged in by the enterprise network that is associated with the vendor, and
wherein data minimization is implemented by prohibiting a vendor access to any sensitive data in the enterprise network.
|