| CPC G06Q 20/4016 (2013.01) [G06F 16/9024 (2019.01); G06Q 20/12 (2013.01)] | 23 Claims |
|
1. A computer-implemented method comprising:
a computer system interacting in real-time with a user-device, including the computer system receiving a web resource request from the user device and the computer system receiving information from the user device, the information including a first attribute comprising at least one of: an email address; an IP address associated with the user device; or billing information;
a computer receiving the information provided to the computer system by the user device, the information including the first attribute;
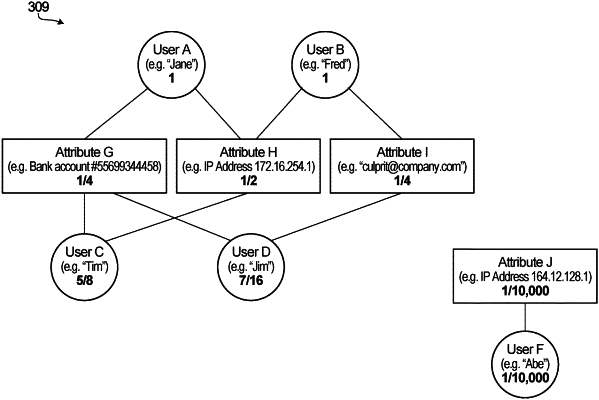
the computer accessing from memory in real-time at least a portion of a graph, wherein the graph includes: (1) user nodes, wherein each user node corresponds to a respective different user, and (2) attribute nodes, wherein each attribute node corresponds to a respective different attribute; wherein each user node is connected to each attribute node associated with an attribute of that user, and different users sharing a same attribute are both connected to the attribute node associated with the same attribute;
the computer determining in real-time, based on the attribute nodes of the graph, that the first attribute received from the user device matches a second attribute stored in a particular attribute node of the graph, the second attribute stored in the particular attribute node in the graph being known to the computer system prior to receiving the information from the user device, and the particular attribute node having an associated attribute untrustworthiness value that is indicative of a first level of untrustworthiness;
the computer modifying the graph in the memory in real-time to add a new user node for a user associated with the user device, including connecting the new user node to both the particular attribute node and to at least one other attribute node corresponding to at least one other attribute present in the information received from the user device;
the computer assigning, to the new user node of the graph in real-time, a user untrustworthiness value that is indicative of a second level of untrustworthiness, the user untrustworthiness value based at least on the attribute untrustworthiness value associated with the particular attribute node, and the user untrustworthiness value representative of a probability that the user device is interacting with the computer system to perform fraudulent activity via the computer system;
the computer determining, using the user untrustworthiness value representative of the probability, that the user device may be interacting with the computer system to perform the fraudulent activity; and
responsive to the computer determining that the user device may be interacting with the computer system to perform the fraudulent activity:
the computer generating, in real-time, web content different from the web resource requested by the user device, and the computer providing, to the user device via the computer system, the web content instead of the web resource requested by the user device, wherein the user device is unable to access the web resource prior to providing input requested by the web content, and wherein the web content is based, at least in part, on the user untrustworthiness value;
the computer receiving the input requested by the web content, wherein the input originates from the user device;
based on the input requested by the web content and received by the computer, the computer recalculating, in real-time, the user untrustworthiness value assigned to the new user node of the graph to result in an updated user untrustworthiness value;
based on the updated user untrustworthiness value, the computer causing the computer system to provide the web resource to the user device, and the computer system providing, to the user device, the web resource.
|