| CPC G06N 20/00 (2019.01) [G06F 18/214 (2023.01); G06F 18/23 (2023.01); G06F 18/23213 (2023.01); G06F 18/24137 (2023.01); H04L 63/0236 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A computer implemented method, comprising:
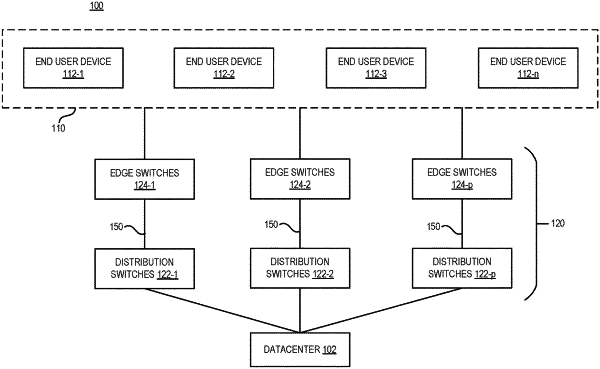
retrieving, from a network device, a first set of samples associated with a first set of time intervals, based at least in part on network traffic over a network, for a first predetermined period of time, wherein each sample associated with a respective time interval comprises a distribution of packets based on packet lengths of the packets;
generating, using an unsupervised machine learning mechanism, a first set of clusters of the first set of samples;
determining a first one or more features from the first set of clusters;
in response to retrieving a second set of samples associated with a second set of time intervals, based at least in part on the network traffic, for a second predetermined period of time, generating, using the unsupervised machine learning mechanism, a second set of clusters of the second set of samples;
determining a second one or more features from the second set of clusters;
determining whether the second one or more features determined from the second set of clusters vary as compared to the first one or more features determined from the first set of clusters to detect unclassified traffic in the network traffic; and
upon detecting the unclassified traffic, performing a security action,
wherein each sample of the first set of samples associated with the respective time interval comprises counts of packets having byte lengths for different packet byte length ranges.
|