| CPC G06F 9/3017 (2013.01) [G06F 9/44521 (2013.01); G06F 21/51 (2013.01); G06F 21/54 (2013.01)] | 20 Claims |
|
1. A method, comprising:
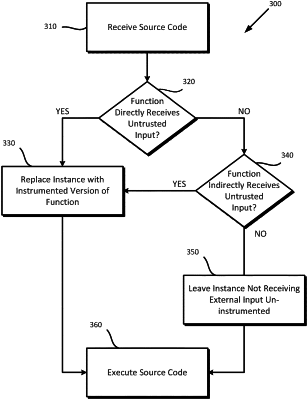
identifying a first instance of a function in a program that receives tainted input data from an untrusted source, the first instance of the function being a subset of all instances of the function; and
replacing, during runtime of the program, the first instance of the function receiving the tainted input data, being the subset of all the instances of the function, with an instrumented version of the function that calls a marking function that indicates an output of the instrumented version of the function includes the tainted input data received from the untrusted source.
|