| CPC G06F 9/30145 (2013.01) [G06F 9/45533 (2013.01); G06F 9/545 (2013.01)] | 21 Claims |
|
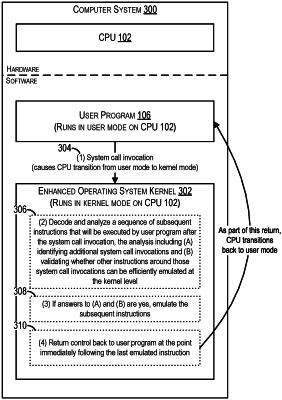
1. A method comprising:
receiving, by an operating system (OS) kernel of a computer system, an invocation of a system call by a user program running on the computer system;
fetching, by the OS kernel, a plurality of subsequent instructions that will be executed by the user program after the invocation of the system call;
decoding, by the OS kernel, the plurality of subsequent instructions into a plurality of decoded instructions; and
analyzing, by the OS kernel, whether:
the plurality of decoded instructions includes an additional system call invocation; and
all other decoded instructions that appear in the plurality of decoded instructions between the invocation of the system call and the additional system call invocation are viable for emulation by the OS kernel.
|