| CPC G06F 21/604 (2013.01) [G06F 21/606 (2013.01); H04L 63/104 (2013.01); H04L 63/20 (2013.01); H04W 4/185 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2141 (2013.01); H04L 63/0428 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for creating digitally secured data, comprising:
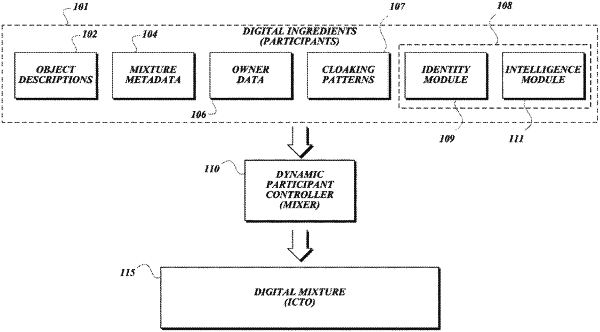
initializing a dynamic participant controller (DPC);
receiving, by the DPC, a set of digital participant data;
constructing, by the DPC and using the set of digital participant data, a computer-based intelligent cipher transfer object (ICTO);
applying, by the DPC, an outer cloaking pattern to the set of digital participant data in the ICTO using an interim ruleset;
adding, by the DPC, owner data elements to the ICTO;
replacing, by the DPC, the interim ruleset with owner-specific rules;
applying, by the DPC, an inner cloaking pattern to the ICTO based at least in part on the owner-specific rules, thus creating a secure set of digital participant data.
|