| CPC G06F 21/577 (2013.01) [G06F 16/2471 (2019.01); G06F 16/287 (2019.01); G06F 21/552 (2013.01); G06F 2221/2101 (2013.01)] | 20 Claims |
|
1. A system for unified cyberthreat intelligence searching comprising:
a data lake comprising a plurality of search clusters that provide access to a plurality of respective databases, wherein a first search cluster provides access to curated threat intelligence information and a second search cluster provides access to raw conversation data from at least one communication channel, wherein the first search cluster is communicably coupled to at least one analyst device and is configured to receive and store a curated threat report from the at least one analyst device, wherein the at least one analyst device is configured to:
cause a graphical user interface to be displayed, the graphical user interface comprising intelligence data;
receive at least one input from an analyst via the graphical user interface;
modify the intelligence data via the at least one input to generate the curated threat report; and
transmit the curated threat report to the first search cluster; and
a server comprising non-transitory computer-readable instructions which, when executed by at least one processor, cause the server to perform a process operable to:
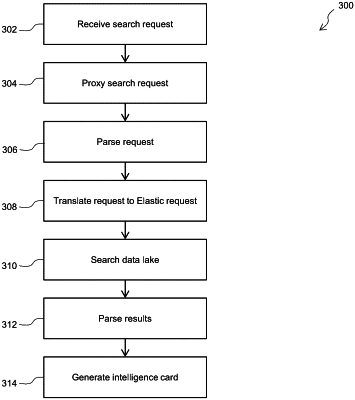
receive a query from a client endpoint;
parse the query for at least one keyword;
translate the parsed query into a plurality of search requests for the plurality of search clusters;
search each of the plurality of search clusters with a respective search request;
generate a plurality of intelligence cards, each intelligence card comprising a result from one of the plurality of search clusters, including at least one result from the first search cluster based on the curated threat report;
cause the plurality of intelligence cards to be displayed on the client endpoint;
receive a selection of at least one of the plurality of intelligence cards from the client endpoint; and
generate an investigation with the selected intelligence cards.
|