| CPC G06F 21/575 (2013.01) [G06F 9/4416 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
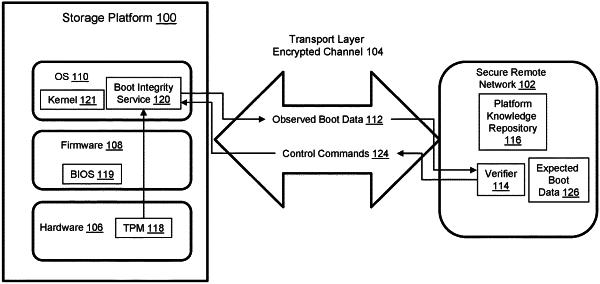
1. An apparatus comprising: a storage platform comprising at least one compute node comprising at least one general purpose processor, memory, a secure cryptoprocessor, non-volatile storage, and a boot integrity service loaded during a boot sequence, the boot integrity service configured to: obtain, from the secure cryptoprocessor, observed boot data values comprising:
a first hash that uniquely represents programs running at load/run BIOS POST;
a second hash that uniquely represents programs running at load/run bootloader;
a third hash that uniquely represents programs running at load/run kernel; and
a fourth hash that uniquely represents the programs running at load/run runlevel programs;
provide the observed boot data values comprising the first, second, third and fourth hashes as part of platform configuration register content included within a trusted platform quote along with a nonce and an attestation integrity key (AIK) signature, to a remote verifier in a secure remote network that does not contain the storage platform for comparison with expected boot data values; and
responsive to a control command from the remote verifier generated in response to mismatch between the observed boot data values and the expected boot data values, limit functionality of the storage platform.
|