| CPC G06F 21/572 (2013.01) [H04L 9/0643 (2013.01); G06F 2221/033 (2013.01); G06F 2221/2149 (2013.01)] | 20 Claims |
|
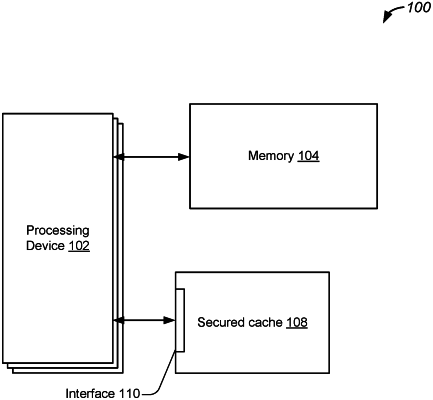
1. A method comprising:
performing, using one or more processing elements of a secured execution environment, a first cryptographic computation on a portion of code to generate a result;
determining, using the one or more processing elements, if a verified result is stored in a secured storage location;
in response to determining that the verified result is stored, retrieving the verified result from the secured storage location;
in response to determining that no verified result is stored, determining, using the one or more processing elements, an authenticated version of a cryptographic value, the authenticated version of the cryptographic value being determined based on a signature computation and a second cryptographic computation that is an asymmetric cryptographic computation; and
determining, using the one or more processing elements, if the result of the first cryptographic computation is verified based, at least in part, on a comparison of the result with the verified result or the authenticated version of the cryptographic value.
|