| CPC G06F 21/35 (2013.01) [G06F 21/44 (2013.01); H04L 9/0861 (2013.01); H04L 9/0872 (2013.01); H04L 9/3271 (2013.01); H04L 9/3297 (2013.01); H04L 63/0492 (2013.01); H04L 63/061 (2013.01); H04W 4/80 (2018.02); H04W 12/0471 (2021.01); H04L 2209/805 (2013.01)] | 28 Claims |
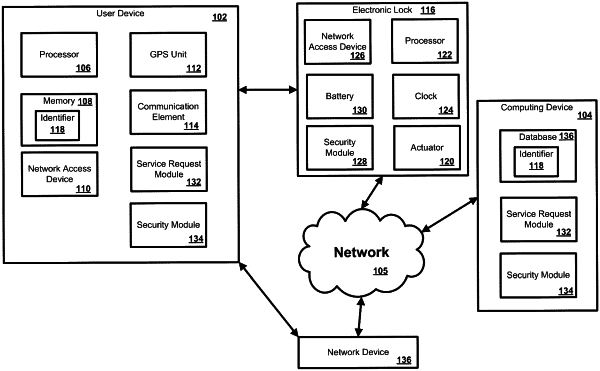
|
1. A method comprising:
receiving, via a first user device associated with a first user, a first input associated with a submission of a first service request,
wherein the first service request defines a first time window during which the first service request can be opened and access to a first security device is authorized;
receiving, via a second user device associated with a second user, a second input associated with a submission of a second service request,
wherein the second service request defines a second time window during which the second service request can be opened and access to a second security device is authorized;
assigning the first service request and the second service request to a third user device associated with a third user,
wherein the first service request and the second service request are accessible via the third user device;
selecting, via the third user device, the first service request;
receiving a third input associated with a request to access the first security device during the first time window,
wherein the request to access the first security device is associated with an opening of the first service request during the first time window, and
wherein the third input is received in response to a first movement associated with the third user device;
sending, based on a proximity of the third user device to the first security device, the request to access the first security device;
receiving, based on the request to access the first security device and the proximity of the third user device to the first security device, first authentication information,
wherein the first authentication information comprises first timing information;
determining, based on the first timing information, a first security key,
wherein the first security key is associated with the first time window and is valid during at least a portion of the first time window, and
wherein determining the first security key comprises associating the first timing information with the first time window that is associated with the first security key;
sending, based on the proximity of the third user device to the first security device and at least a portion of the first authentication information and the first security key, a first authentication response;
accessing, based on the first authentication response matching a first expected authentication response, the first security device; revoking the first security key,
wherein revoking the first security key is based on a closing of the first service request, and
wherein revoking the first security key causes access to the first security device to be revoked;
selecting, via the third user device, the second service request;
receiving a fourth input associated with a request to access the second security device during the second time window,
wherein the request to access the second security device is associated with an opening of the second service request during the second time window, and
wherein the fourth input is received in response to a second movement associated with the third user device;
sending, based on a proximity of the third user device to the second security device, the request to access the second security device;
receiving, based on the request to access the second security device and the proximity of the third user device to the second security device, second authentication information,
wherein the second authentication information comprises second timing information;
determining, based on the second timing information, a second security key,
wherein the second security key is associated with the second time window and is valid during at least a portion of the second time window, and
wherein determining the second security key comprises associating the second timing information with the second time window that is associated with the second security key;
sending, based on the proximity of the third user device to the second security device and at least a portion of the second authentication information and the second security key, a second authentication response;
accessing, based on the second authentication response matching a second expected authentication response, the second security device;
revoking the second security key,
wherein revoking the second security key is based on a closing of the second service request, and
wherein revoking the second security key causes access to the second security device to be revoked.
|